Are you wondering about the critical importance of a SOC2 report for your organizations security and trust? This comprehensive SOC2 guide unpacks what a SOC2 audit entails, why it has become an indispensable benchmark for modern businesses, and how achieving compliance can significantly boost your competitive edge and customer confidence. We delve into the Trust Services Criteria, the differences between Type 1 and Type 2 reports, and the structured pathway to navigate your audit process effectively. Understanding this framework is not just about meeting regulatory requirements; its about building a robust security posture that protects sensitive data, fosters client trust, and ensures operational resilience in an increasingly digital world. This guide offers actionable insights for businesses of all sizes looking to secure their future by prioritizing data integrity and privacy, making it a must-read for leaders, IT professionals, and compliance officers alike. Discover the foundational elements of a SOC2 report and learn how to proactively address security concerns before they become problems, ensuring your operations remain trustworthy and secure.
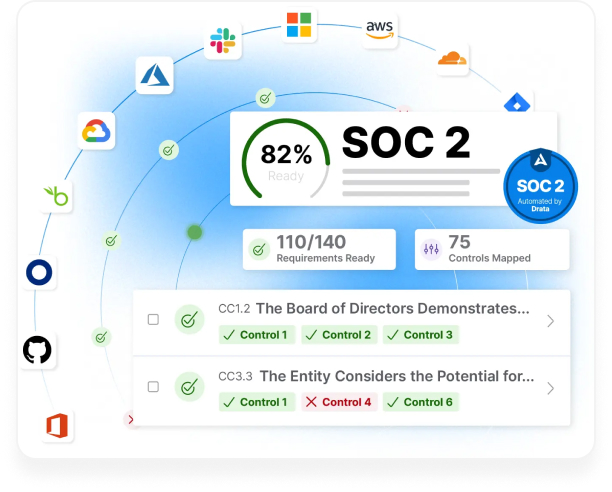
When we talk about data security in todays fast-paced digital landscape, a crucial question often surfaces: What exactly is a SOC2 report, and why does your business desperately need this SOC2 guide right now? Many organizations, especially those providing services that store or process customer data, ponder who needs to get a SOC2 report, what it entails, when the right time to start the process is, where these standards apply, why it is so important for building trust, and how one successfully navigates the audit. Simply put, a SOC2 report serves as a rigorous, independent assessment of a service organizations internal controls related to security, availability, processing integrity, confidentiality, and privacy of user data. It provides assurance to customers and stakeholders that your systems are designed to keep their sensitive information safe and your services reliable. Failing to understand or pursue a SOC2 audit can leave your business vulnerable to data breaches, reputational damage, and a significant loss of customer confidence, making this guide an essential resource for securing your operational future.
The Essence of SOC2 Guide: What It Means for Your Business
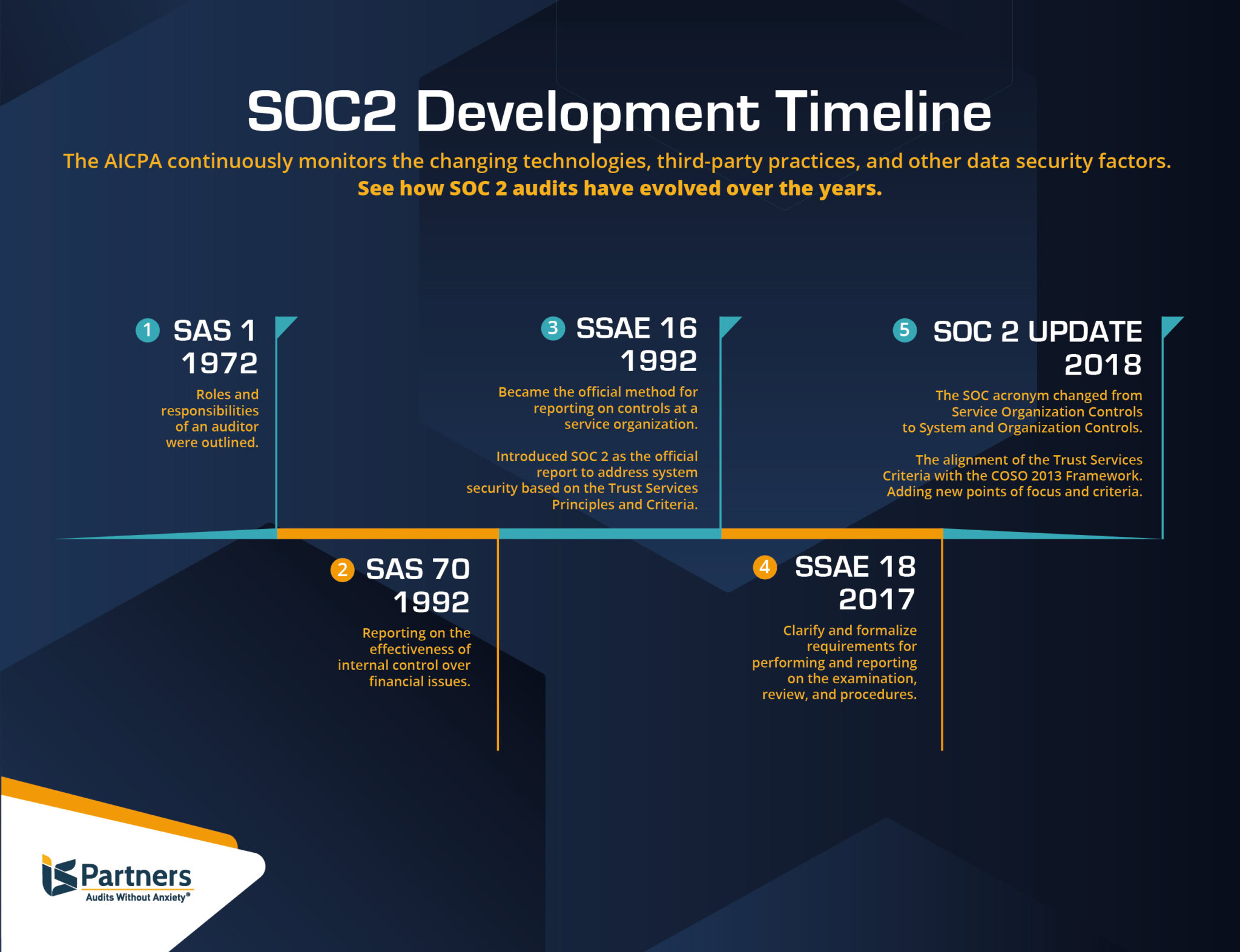
Understanding the core principles behind a SOC2 report is like grasping the foundational pillars of trust in the digital age. What exactly defines a SOC2 report, and how does this SOC2 guide clarify its importance? A Service Organization Control 2 (SOC2) report, developed by the American Institute of Certified Public Accountants (AICPA), offers a standardized way for service organizations to communicate their control environment to their customers and other stakeholders. Who really benefits from this rigorous assessment? Predominantly, it is businesses that handle customer data, such as SaaS providers, data centers, and managed IT service companies, who want to demonstrate their commitment to data protection. When should an organization consider pursuing a SOC2 audit? Ideally, before prospective clients even ask for it, as it serves as a proactive signal of security maturity. Where do these audits apply? They apply globally to any service organization, regardless of physical location, that manages sensitive information for others. Why embrace SOC2? Because it directly impacts customer trust and provides a competitive advantage, proving you take security seriously. How does one achieve compliance? It involves a detailed audit process, examining your systems and controls against specific criteria. This comprehensive look helps your organization not only meet market expectations but often exceed them, transforming security from a mere checkbox into a fundamental operational strength that speaks volumes about your reliability and dedication to protecting client assets, ultimately strengthening your market position.
Navigating the Trust Services Criteria with Your SOC2 Guide
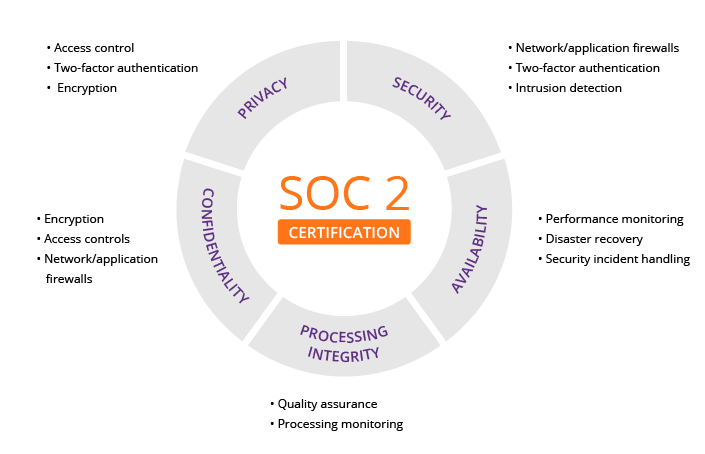
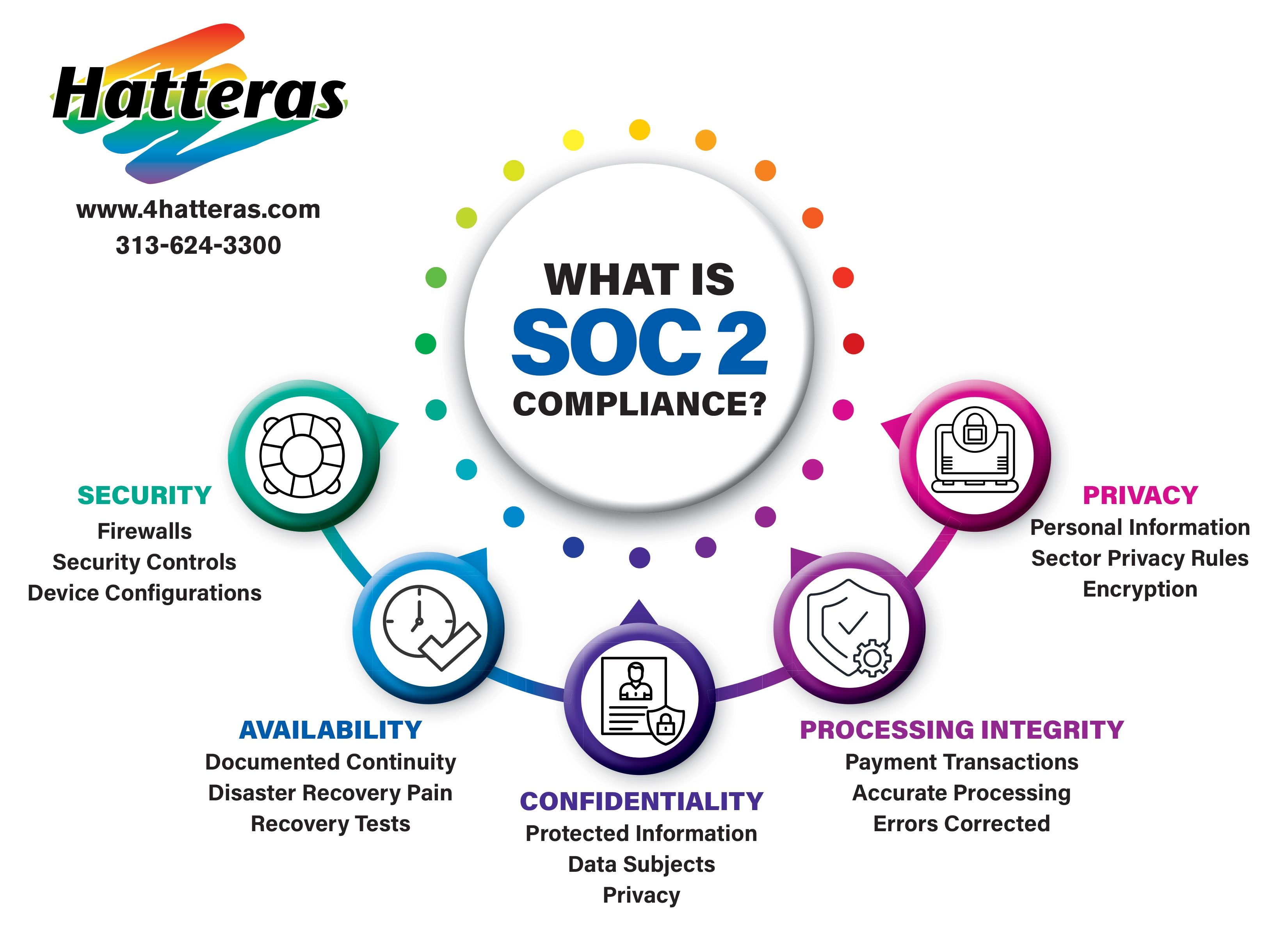
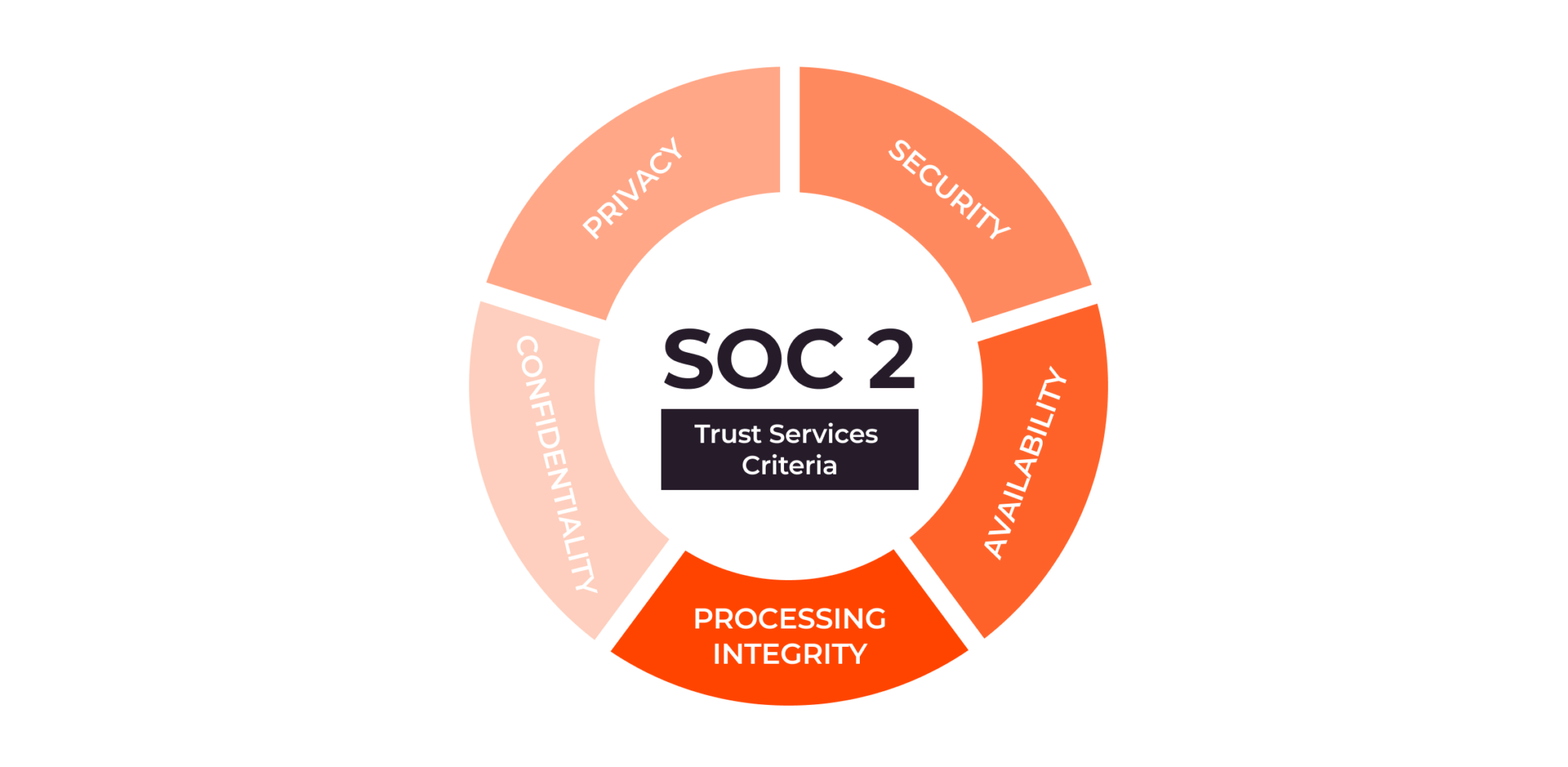
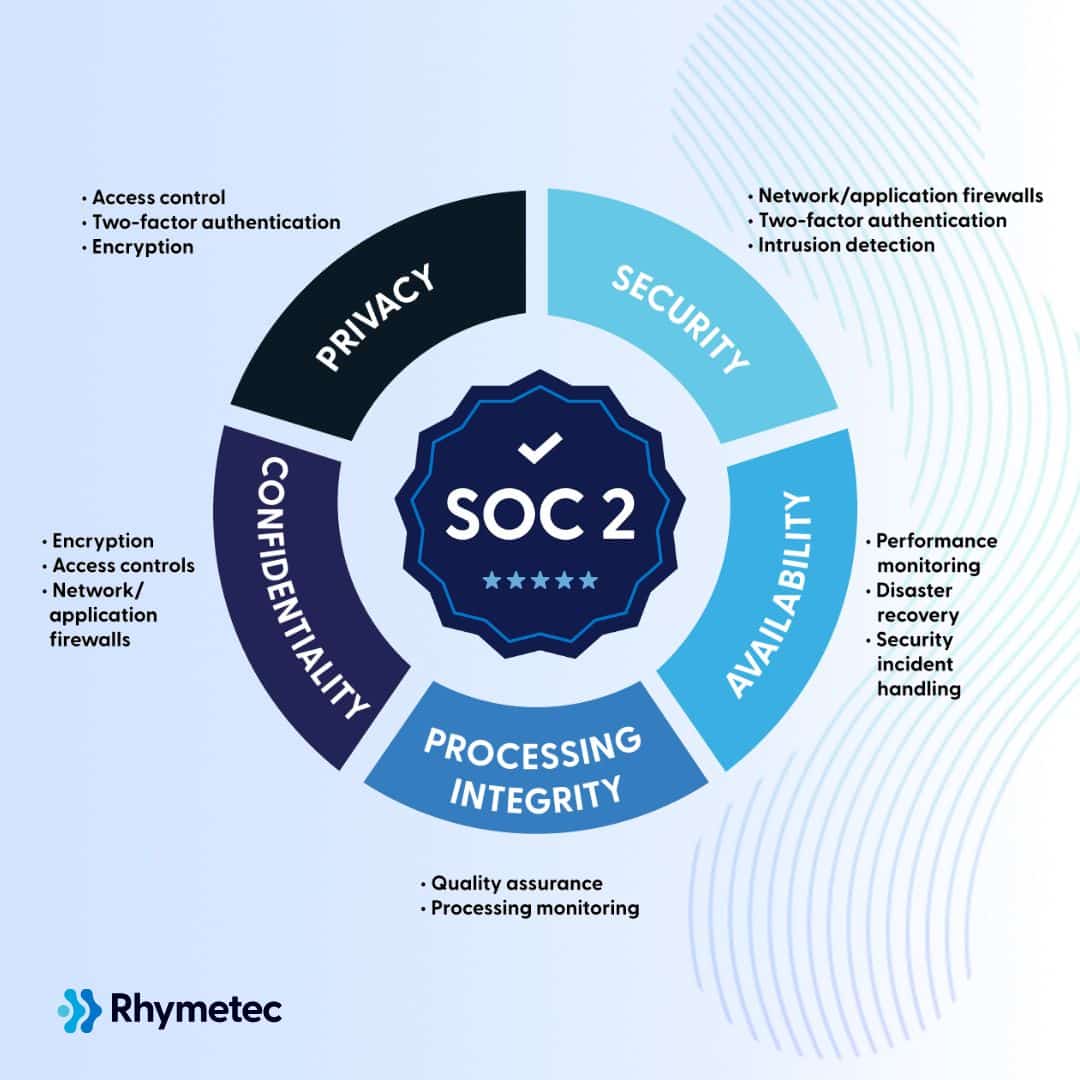
Diving deeper into the SOC2 framework, you quickly encounter the Trust Services Criteria (TSC), which form the bedrock of any successful audit. What are these criteria, and how does this SOC2 guide help you interpret them for your organization? The TSC are a set of principles that auditors use to evaluate the design and operating effectiveness of a service organizations controls. Who defined these crucial guidelines? The AICPA developed them to provide a consistent framework across industries. There are five main criteria: Security, Availability, Processing Integrity, Confidentiality, and Privacy. Security, often considered the baseline, refers to the protection of system resources against unauthorized access. Availability addresses the operational uptime and accessibility of the system, ensuring users can access services when needed. Processing Integrity focuses on whether system processing is complete, valid, accurate, timely, and authorized. Confidentiality concerns the protection of information designated as confidential, preventing unauthorized disclosure. Privacy pertains to the collection, use, retention, disclosure, and disposal of personal information in conformity with the organization’s privacy notice and generally accepted privacy principles. When do you choose which criteria to include in your audit? Organizations select the criteria most relevant to the services they provide and the data they handle. Where do these criteria make the biggest impact? They guide the implementation of internal controls across all IT infrastructure and business processes. Why are these criteria so important? They provide a structured language for communicating security and compliance posture to clients. How do organizations ensure adherence? Through meticulous policy development, procedural implementation, and ongoing monitoring, making a clear path for every step of the journey towards compliance. This structured approach helps in building a robust security environment and communicates your dedication to data protection effectively.
Type 1 vs. Type 2 SOC2 Reports: A Critical Distinction in Your SOC2 Guide
When you embark on your SOC2 journey, a significant decision arises: should you pursue a Type 1 or a Type 2 report, and what does this SOC2 guide reveal about their differences? Understanding this distinction is absolutely critical for setting the right expectations and demonstrating the appropriate level of assurance to your stakeholders. What exactly differentiates a Type 1 from a Type 2 report? A Type 1 report examines the design effectiveness of your controls at a specific point in time, essentially a snapshot of your systems security posture. It tells you if your controls are *designed* correctly to meet the Trust Services Criteria. Who typically opts for a Type 1 report? Organizations just starting their compliance journey or those needing to quickly demonstrate a foundational level of control design often choose this. When is a Type 1 report most appropriate? It serves well as an initial step, offering immediate assurance regarding control design. In contrast, a Type 2 report goes much further, evaluating both the design *and* the operational effectiveness of your controls over a period, typically six to twelve months. This deeper dive assesses whether your controls actually *work* as intended over time. Where do these reports apply differently? While a Type 1 confirms design, a Type 2 provides ongoing assurance, which is usually preferred by mature clients and partners. Why is a Type 2 often considered superior? Because it offers a more comprehensive and trustworthy validation of your security practices over an extended period. How do organizations prepare for each? A Type 1 requires establishing and documenting controls, while a Type 2 demands continuous monitoring and evidence collection over several months. Choosing the right type of report depends on your specific organizational maturity, client requirements, and the level of assurance you aim to provide, guiding your clients through a confident understanding of your security commitments.
| Feature | SOC2 Type 1 Report | SOC2 Type 2 Report |
|---|---|---|
| Purpose | Assess design effectiveness of controls. | Assess design and operational effectiveness of controls. |
| Time Period | A specific point in time. | Over a period (e.g., 6-12 months). |
| Assurance Level | Lower, initial assurance. | Higher, ongoing assurance. |
| Key Question | Are your controls designed correctly? | Are your controls designed and working effectively over time? |
| Use Case | First-time audit, demonstrate foundational controls. | Ongoing compliance, meet stringent client demands, competitive advantage. |
| Effort | Less complex, quicker. | More comprehensive, longer, requires continuous monitoring. |
| Focus | Policy & procedure documentation. | Evidence of control operation. |
Preparing for Your SOC2 Audit: A Step-by-Step SOC2 Guide
Getting ready for a SOC2 audit can feel like a daunting task, but with a structured approach, your business can navigate it successfully. What are the key steps involved in preparing for this crucial assessment, and how does this SOC2 guide simplify the process? Preparation begins long before the auditor arrives, typically involving a readiness assessment to identify gaps in your existing controls. Who should lead this preparation? Often, a dedicated internal team, possibly with external consultants, drives the effort, involving IT, legal, and operational departments. When should you start preparing? Ideally, several months before your target audit date, especially for a Type 2 report, which requires evidence collection over time. Where do you focus your efforts? On documenting policies, implementing procedures, configuring systems, and training staff across all relevant Trust Services Criteria. Why is thorough preparation so important? It minimizes surprises during the actual audit, reduces costs, and increases the likelihood of a clean report. How do you ensure all bases are covered? Conduct internal self-assessments or mock audits to simulate the real thing, gather all necessary evidence, and address any identified weaknesses proactively. This proactive stance not only streamlines the audit process but also fortifies your organizations overall security posture, turning what could be a stressful compliance exercise into a valuable opportunity for operational improvement and strategic growth. By meticulously following these steps, you empower your team to confidently present your control environment, ensuring your SOC2 report reflects the true strength of your security commitment and helps your organization stand out in the marketplace.
Leveraging Your SOC2 Report for Business Growth: The Ultimate SOC2 Guide Advantage
Once you achieve SOC2 compliance, you hold a powerful tool that extends far beyond mere regulatory adherence. How can your business truly leverage its SOC2 report for sustained growth, and what does this SOC2 guide reveal about maximizing its impact? A SOC2 report acts as a universal trust signal, significantly enhancing your credibility with current and prospective clients. Who stands to gain the most from this advantage? Cloud service providers, SaaS companies, and any organization handling sensitive customer data will find it invaluable for sales and marketing. When should you proactively share your report? Integrate it into your sales pitches and onboarding processes for new clients to address security concerns upfront. Where does this report carry the most weight? In competitive markets where data security is a primary differentiator, your SOC2 compliance can be the deciding factor for clients choosing between vendors. Why does it contribute to growth? It streamlines vendor due diligence, accelerates sales cycles, and opens doors to larger, more security-conscious enterprises that demand audited proof of controls. How do you effectively communicate this achievement? Highlight your SOC2 status prominently on your website, in marketing materials, and during client engagements, using it as a testament to your unwavering commitment to data protection and service reliability. This strategic communication transforms your compliance achievement from a necessary expense into a powerful asset, fostering deeper trust, reducing sales friction, and ultimately driving substantial business expansion by assuring clients that their data remains safe and sound in your capable hands, distinguishing your brand in a crowded market.
What is a SOC2 report and why is it vital for modern businesses? A SOC2 report independently assesses a service organizations controls related to data security, availability, processing integrity, confidentiality, and privacy, making it vital for building customer trust and demonstrating a strong security posture in the digital age.
Keywords: SOC2 guide, SOC2 compliance, data security, Trust Services Criteria, audit preparation, business growth, Type 1 report, Type 2 report, information security.
Understanding the SOC2 framework, identifying Trust Services Criteria, differentiating between Type 1 and Type 2 reports, preparing for an audit, leveraging SOC2 for competitive advantage, ensuring data security and privacy, building customer trust through compliance.
Announcing SOC 2 Type II Certified Wowza Graphics Announcing SOC 2 Type II Certified 690x350 1 SOC 2 Compliance Guide Pivotalogic SOC 2 Guide SOC 2 Criteria Soc 2
Stateful Vs Stateless Firewall What S The Difference And Which Is Better SOC Compliance Guide For MSPs SOC 1 Vs SOC 2 Type I Vs Type II.webpSOC 2 Compliance The Complete Guide For SaaS Invimatic Soc2 Guide Controls What Is SOC 2 The Complete Guide A LIGN Infographic SOC 2 Timeline Criteria 2 343x278 Decoding SOC 2 The Essential Guide For 2024 TrustNet Essential Soc 2 Guide For 2024
What Is SOC 2 A Beginners Guide To Compliance Secureframe F51b77be 3b7b 4985 B4aa The Ultimate Guide To SOC 2 What Is SOC 2 The Ultimate Guide To Compliance SOC 2 History Timeline 2048x1573 OT Ultimate Guide To SOC2 Compliance Ebook PDF Business 1SOC2 Complete Guide Arbrielleee Page 1 12 Flip PDF Online 1
The Ultimate Wisconsin Small Business Tax Guide 2025 1 Soc2.svg2022 Ultimate Guide To SOC 2 Ebook PDF Audit Internal Control 1688830780Firecrawl The Web Data API For AI A Step By Step Guide To Getting A SOC 2 Report Hyperproof Hyperproof Step By Step Guide To Getting SOC2 Blog SOC 2(R) Section 3 Information 768x542
Best SOC 2 Type 2 Certified Complaint Solutions 2026 Best SOC 2 CertificateSOC 2 Compliance A Beginner S Guide Rhymetec SOC 2 How To Get SOC 2 Compliance And Maintain It Navigating 9 Key Milestones ImageCompliance Audit Checklist 2026 Definition Key Areas And Steps COMPLIANCE AUDIT CHECKLIST 2026 A COMPLETE READINESS GUIDE FOR
Why Is SOC 2 Compliance Important And What Is It Infographic SOC 2 Compliance Infographic What Is SOC 2 Compliance .webpSOC 2 Compliance Guide Criteria Compliance Process 2026 Complete Guide To SOC 2 Compliance For Businesses Blog A Startup Guide To SOC 2 18 A Startup Guide To SOC 2 Succeed At SOC 2 Guide To SOC 2 Compliance What Is SOC 2 Compliance Web 1536x878
SOC 2 Cheat Sheet SOC Reporting Guide SOC 1 SOC 2 Image The Definitive Guide To SOC 2 Compliance SO SOC 2 Definite Guide 1 0 A Step By Step Guide To Getting A SOC 2 Report Hyperproof Hyperproof Step By Step Guide To Getting SOC2 Blog SOC 2 Type I Vs. SOC 2 Type II 1 279x300 SOC 2 Guide For Tech Firms PDF Information Security Security 1
SOC 2 Compliance A Complete Guide 2024 80642946 A Guide To Soc 2 Compliance A Guide To Compliance Risk Management Example Compliance Thoropass Blog Header SOC 2 Guide 1 POPIA Compliance In South Africa A Complete Guide For 2026 SOC 2 Compliance Steps To Get SOC 2 Certified In 2026 1024x576 Soc Approacheds Guide Image Soc 2 Approaches Guide
SOC 2 Guide 22 Rac 1772 Soc 2 Aicpa Update Smsi A Step By Step Guide To Getting A SOC 2 Report Security Boulevard Hyperproof Step By Step Guide To Getting SOC2 Blog SOC 2 Report Sections 1024x730 What Is Soc 2 A Complete Guide To SOC 2 Compliance Gcore What Is Soc 2 Compliance 2 2048x1002 SOC 2 In 2024 Your Ultimate Guide SOC 2 2024 1